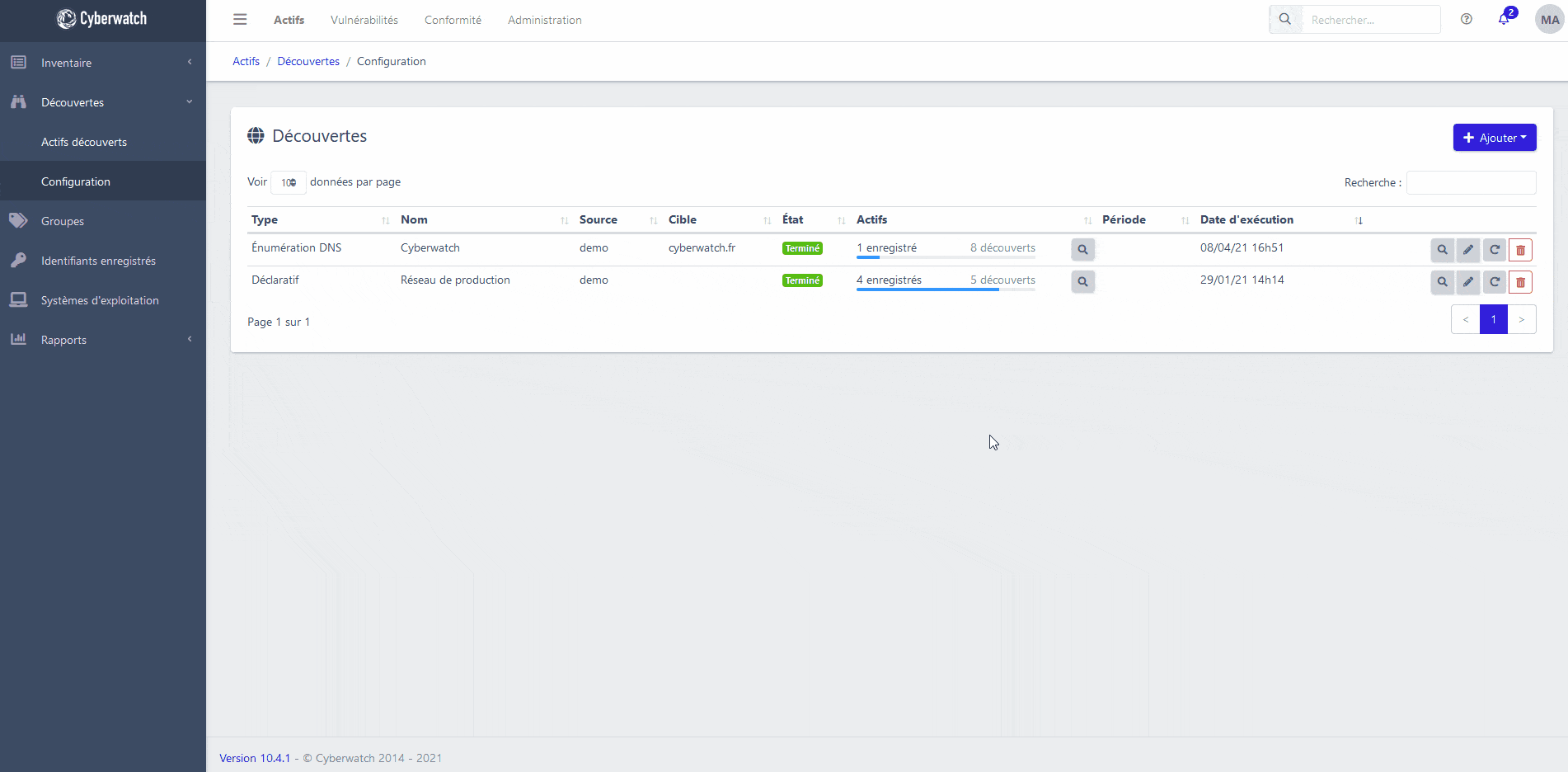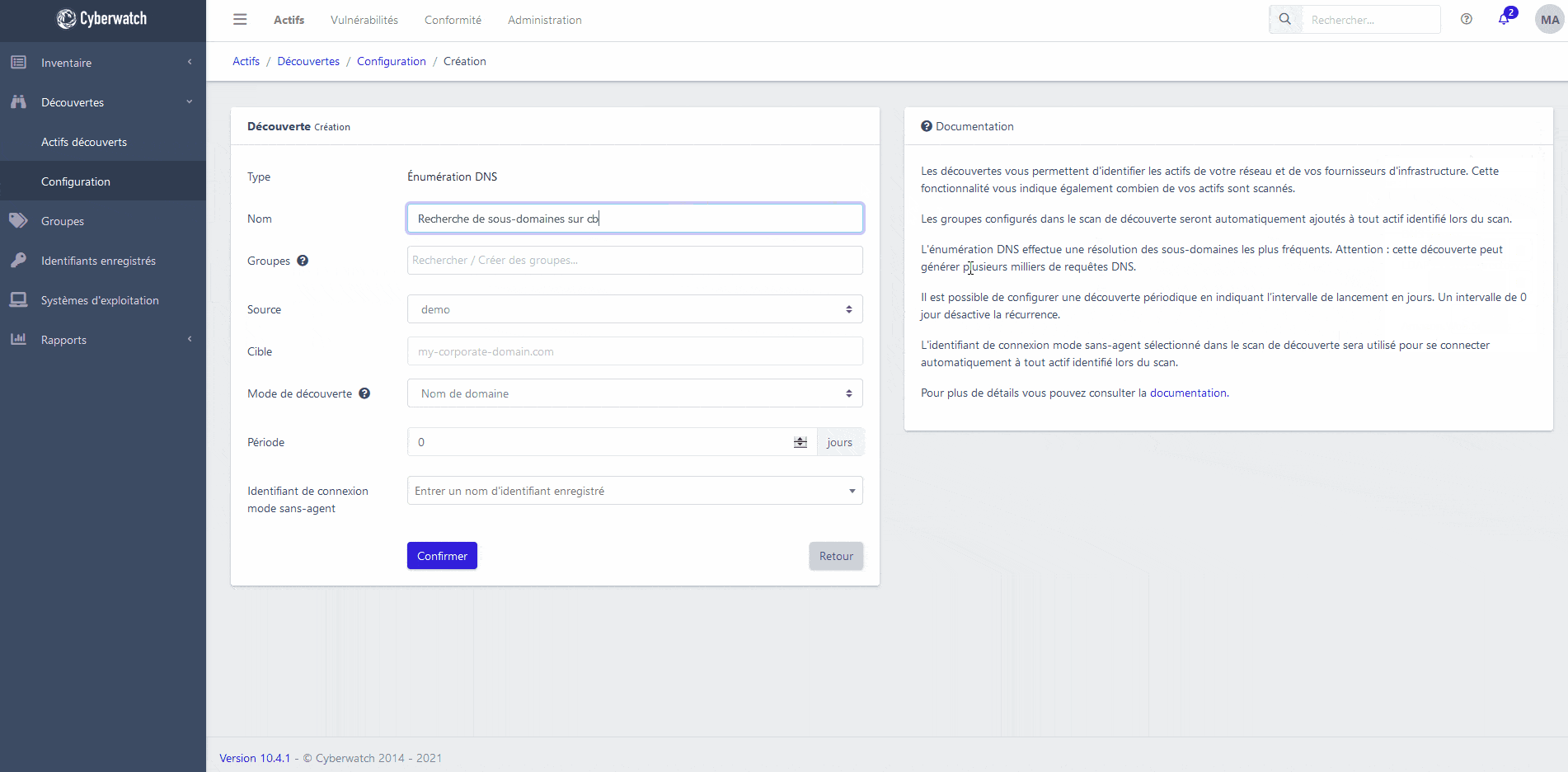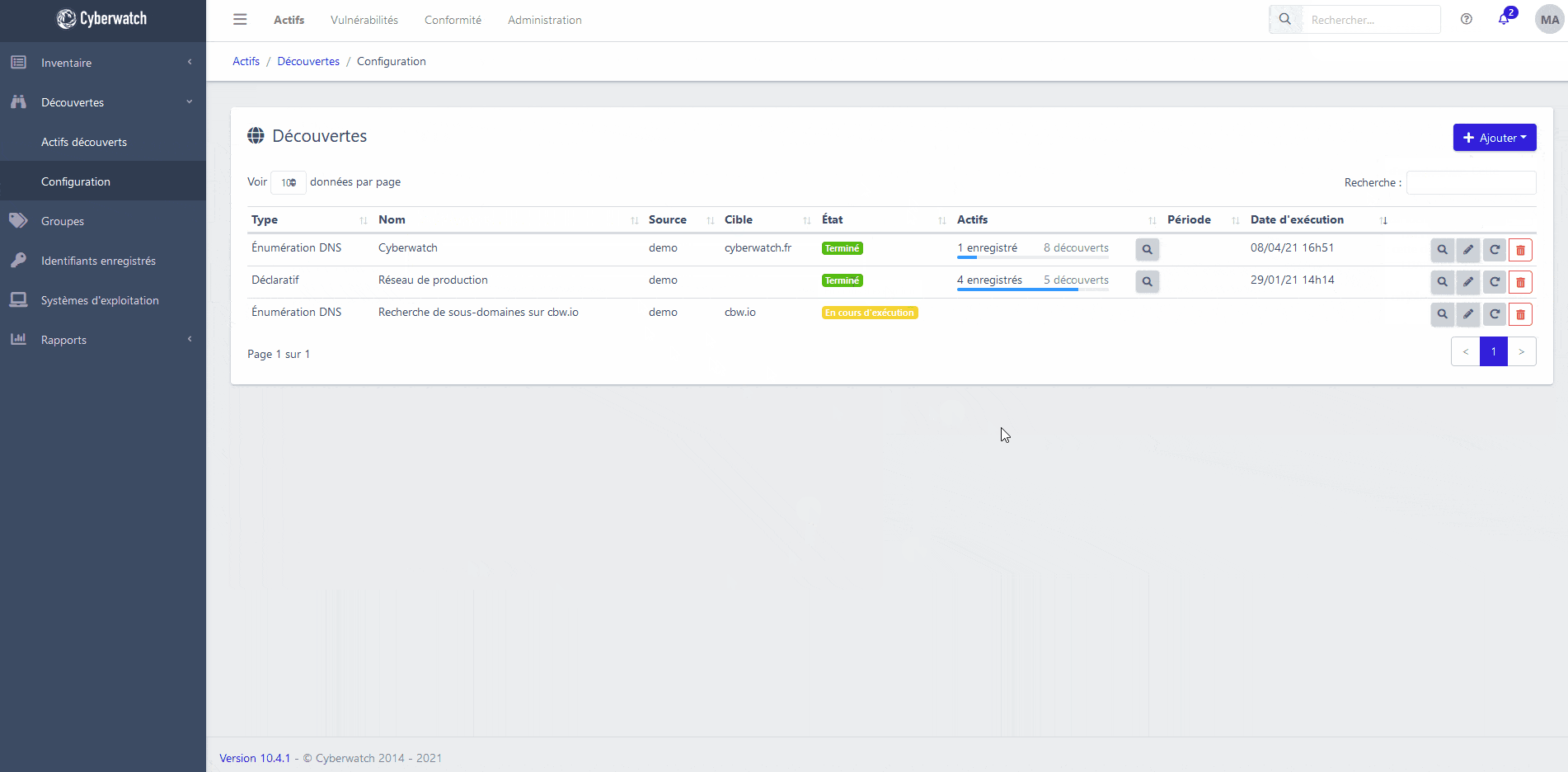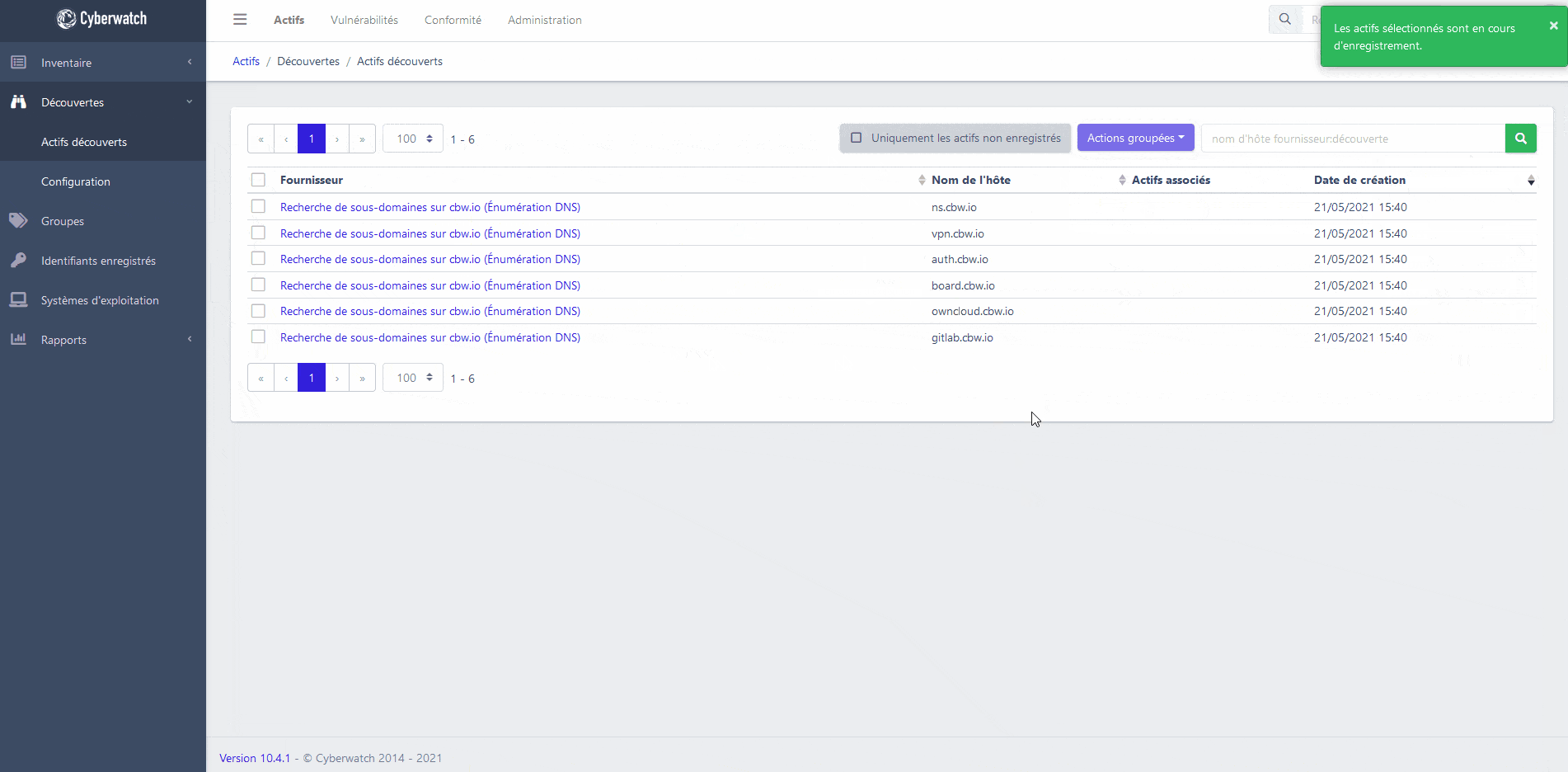
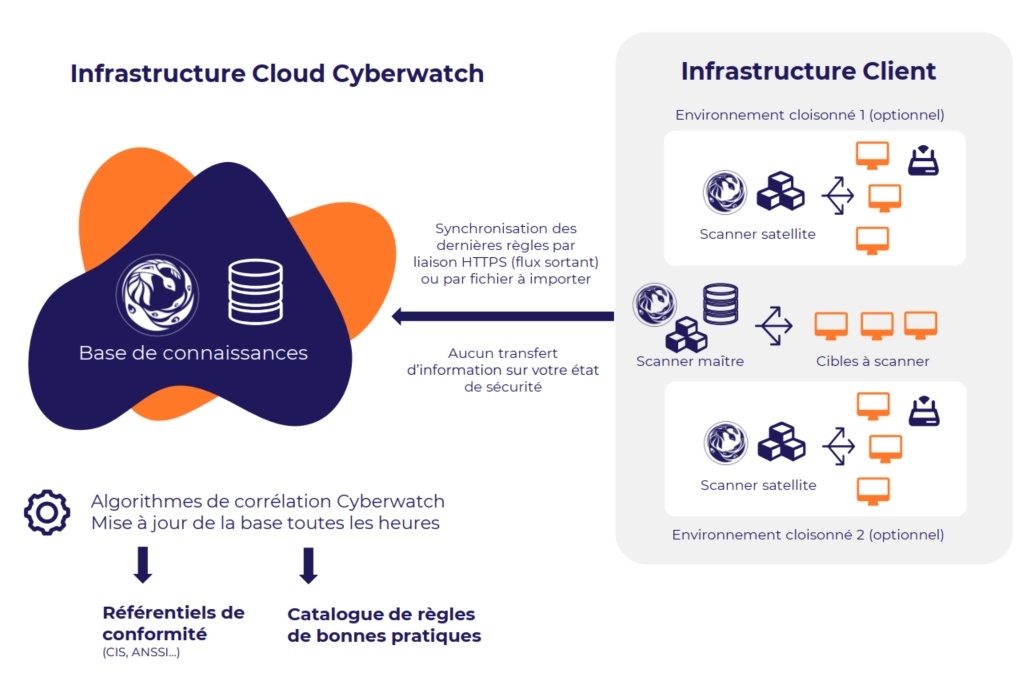
Cyberwatch platform
2 complementary solutions
for corporate cyber security
Vulnerability Manager
From detection to correction of vulnerabilities
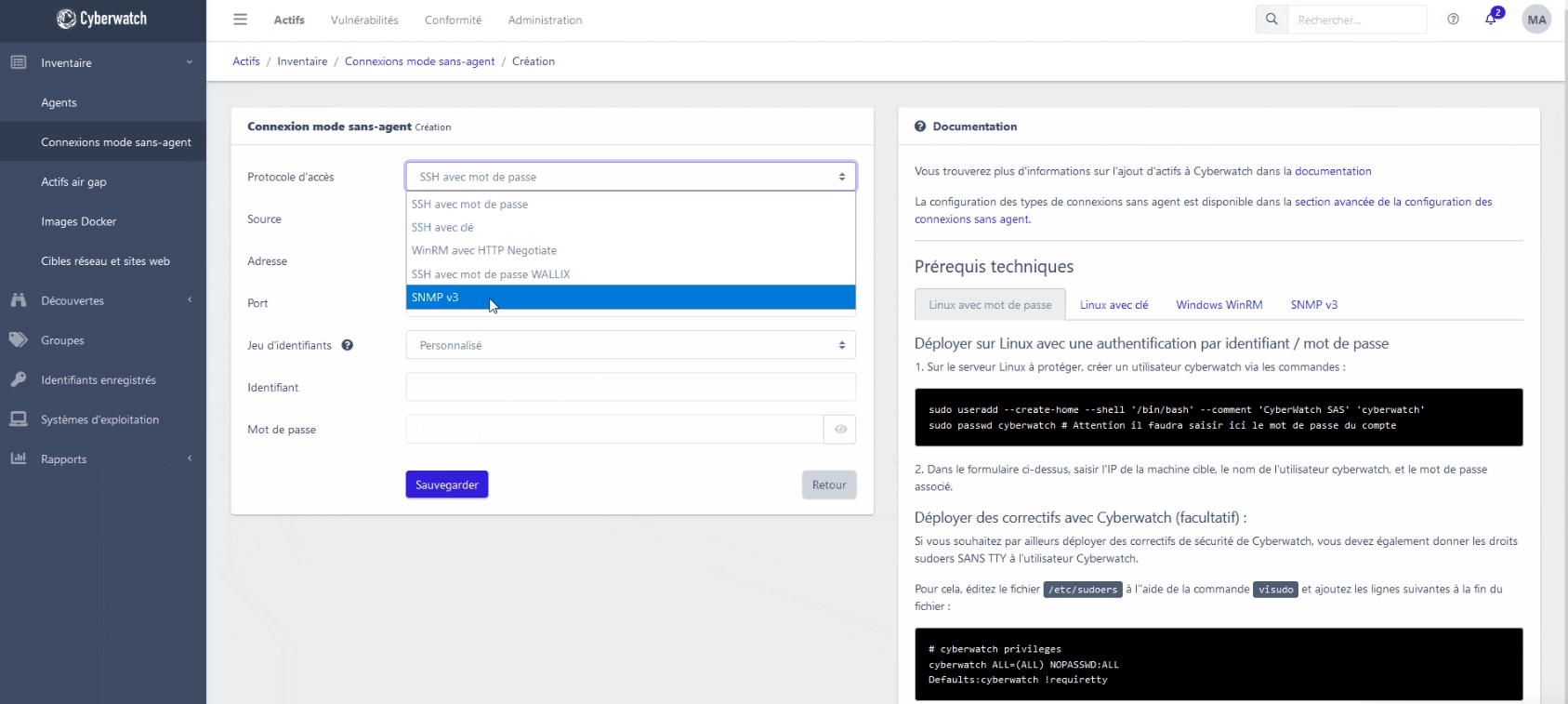
Vulnerability Manager helps you manage your vulnerabilities by giving you a global and continuous view of your vulnerabilities, with detection, prioritization, and remediation :
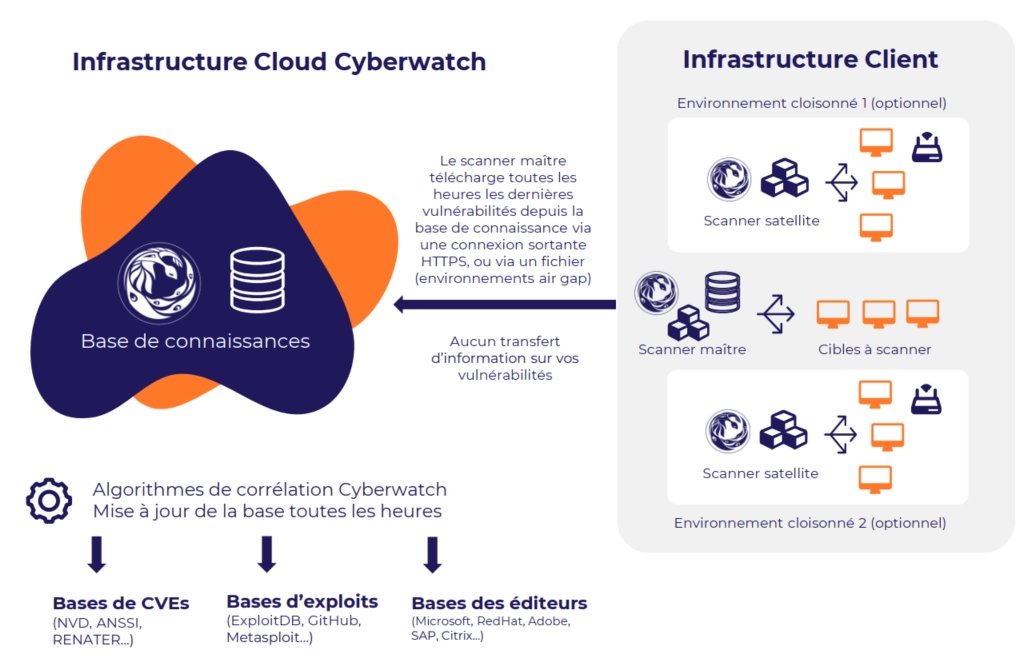
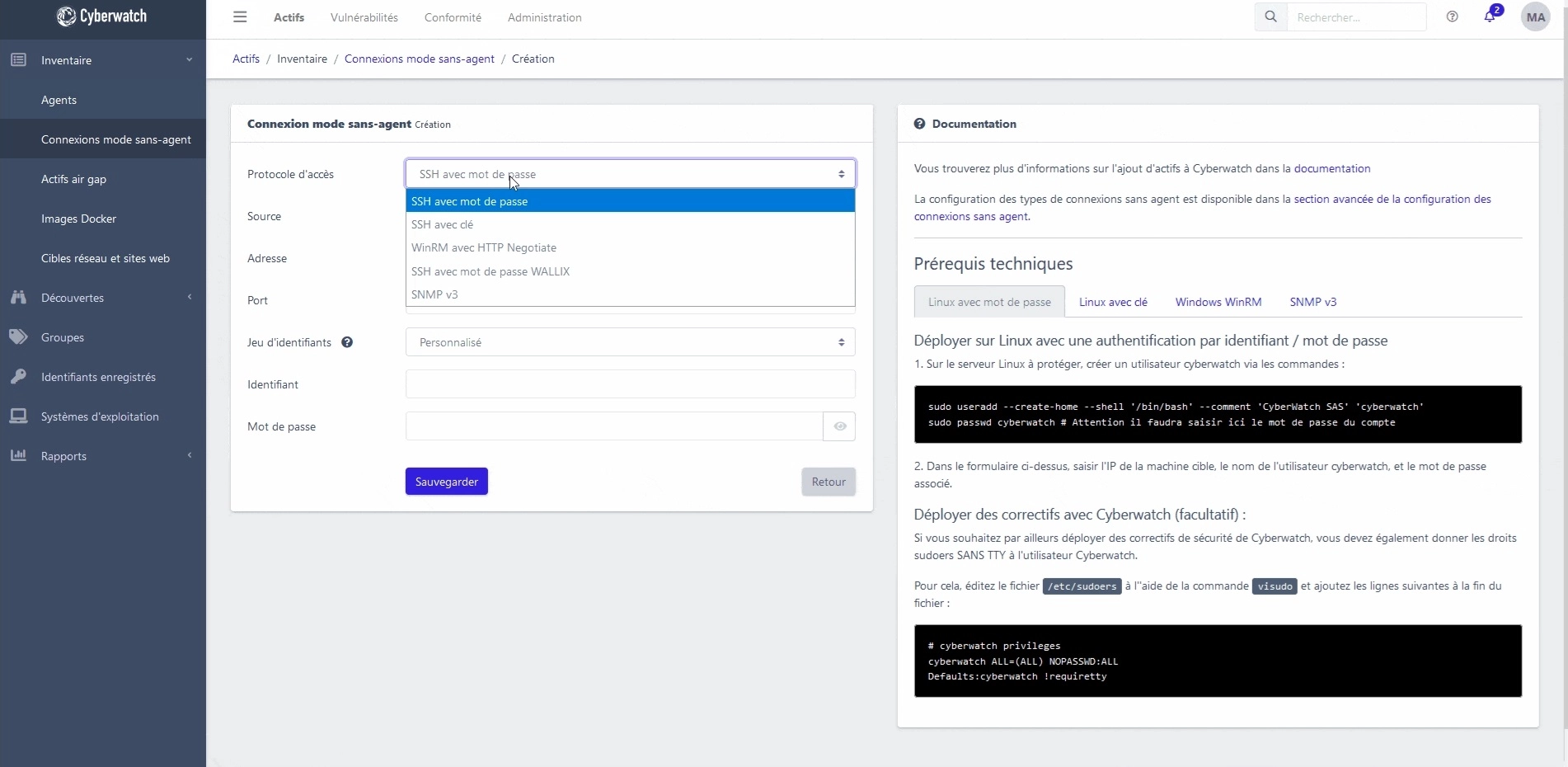
- Have access to a knowledge base of vulnerabilities, hosted within your infrastructure or in SaaS mode,
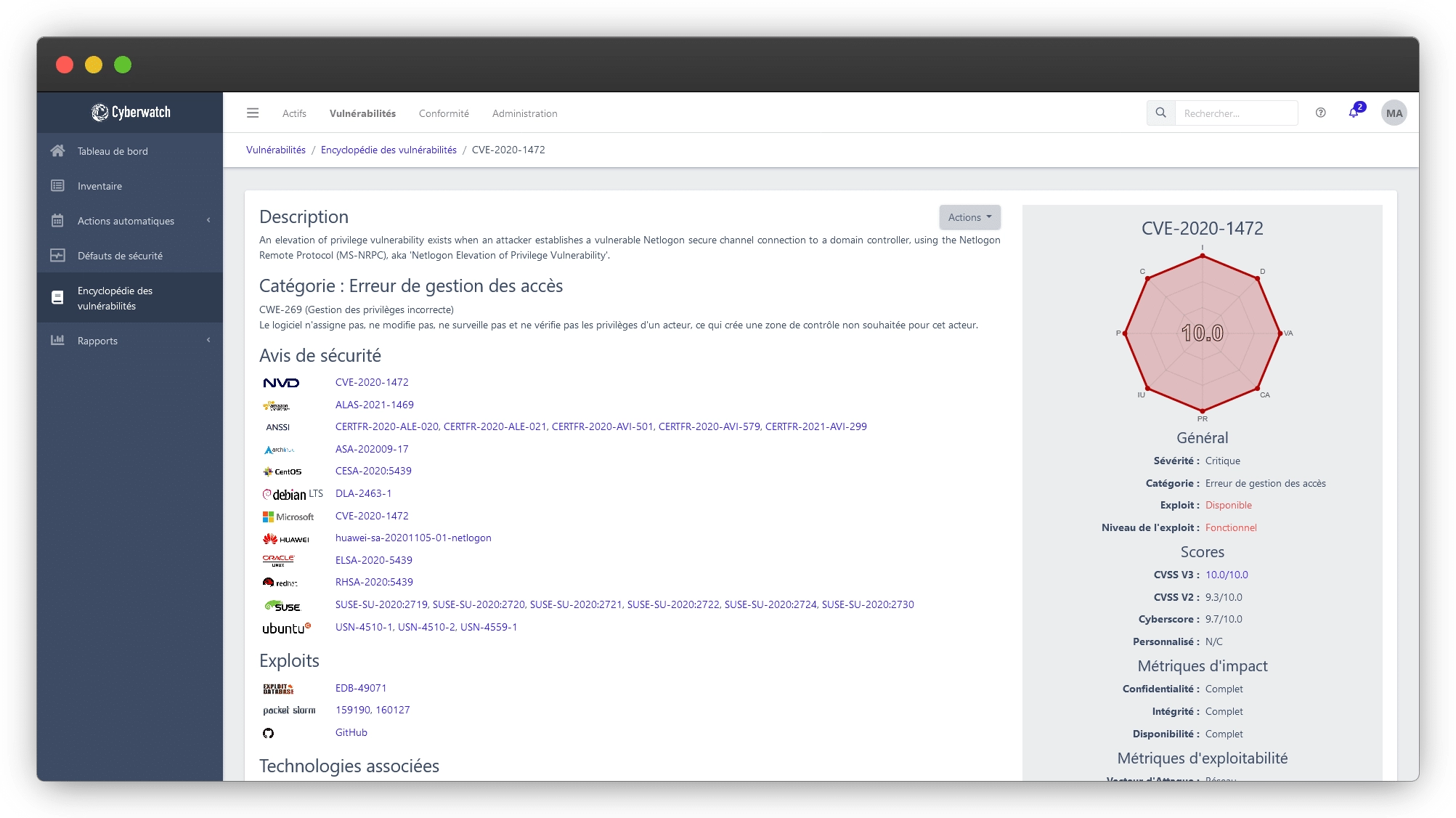
- Prioritize risks and receive only relevant information,
- Identify the vulnerabilities that are easiest to attack and have the greatest impact on your information system.
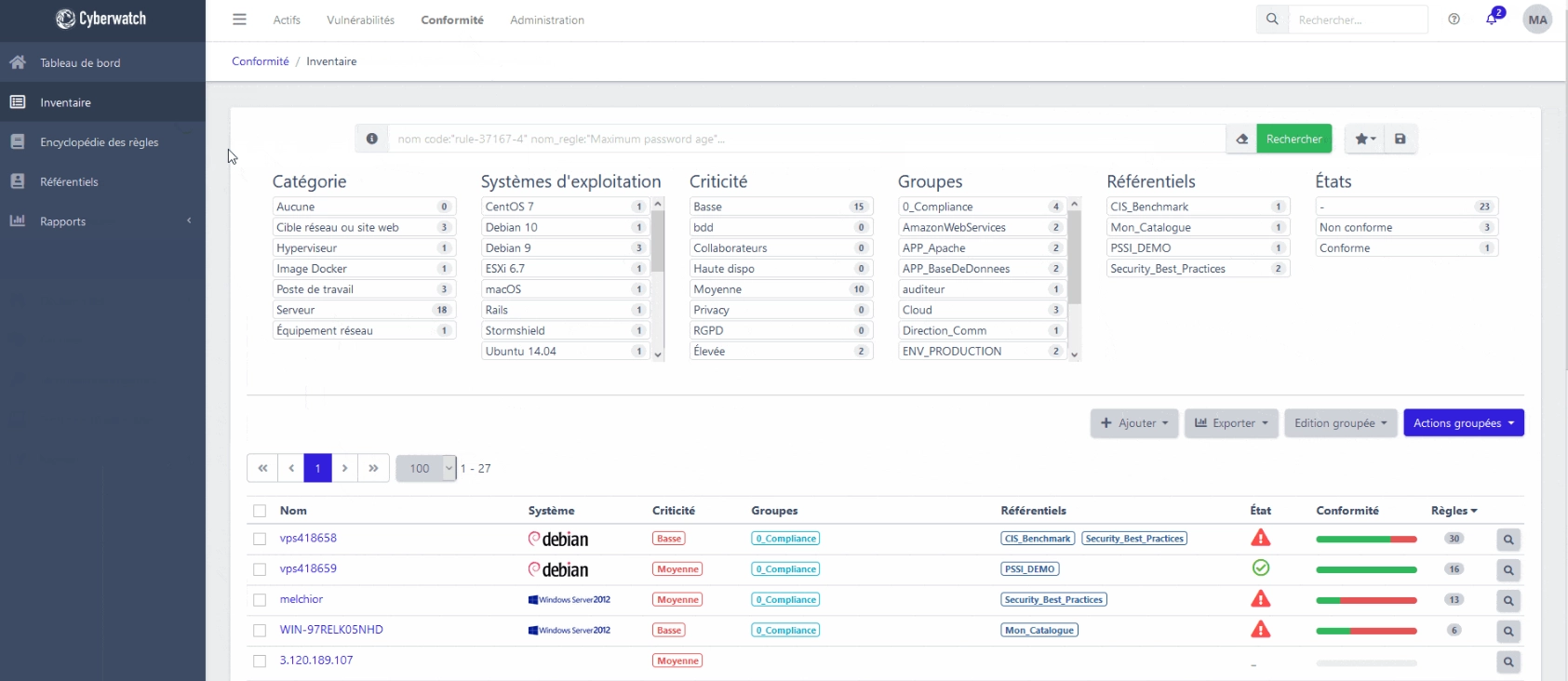
Compliance Manager
The compliance control tool that adapts to your requirements
Cyberwatch Compliance Manager is an optional add-on module to the Vulnerability Manager solution.
It helps you define and achieve your compliance objectives, based on international or customized benchmarks, with total simplicity:
- Managing your compliance is simplified,
- The solution adapts perfectly to your Information Systems Security Policy,
- You are free to use standard market repositories, or to create your own compliance rules.